Android Application Exploitation Challenges
-
Android security specialists
-
Bug bounty hunters
-
Security engineers and developers
Explore the Challenges
What’s Inside?
FactsDroid: Your Universal Knowledgebase
Craving a smarter way to soak up bite-sized knowledge? Say hello to FactsDroid, your sleek and modern companion for discovering mind-blowing facts anytime, anywhere. Built with a stunning Material 3 design and fluid animations, FactsDroid curates random facts from reliable sources and presents them in an engaging, informative format.
Love what you learn? Rate each fact using a 5-star system and save your favorites to a private vault. Thanks to its encrypted local database, your fact collection stays secure and just for you.
Wrapped in vibrant gradients and an intuitive layout, FactsDroid turns everyday curiosity into a fun, stylish experience.
Objective
Learn the art of network interception. Your goal is to intercept the network traffic generated by FactsDroid in a tool that supports dynamic tampering with network traffic such as Burp Suite or Charles Proxy. You should be able to view and modify the API requests and responses between FactsDroid and the backend server without statically patching the provided APK.
Successfully implement a Machine-in-The-Middle (MITM) attack that allows you to manipulate the facts being displayed to the user, potentially inserting custom content or modifying the retrieved facts before they reach the application.
Successfully completing this challenge demonstrates important skills in network security analysis, understanding of mobile app API interactions, and highlights the importance of proper certificate validation and network traffic encryption in mobile applications.
Restrictions: Your solution must work without statically modifying the original APK file and should demonstrate the complete interception workflow, from setup to successful traffic interception. The approach should be applicable to modern Android versions (Android 14+) and focus specifically on network traffic interception techniques.
At no point are you allowed to modify the “request” sent to the backend server. Exploiting the backend server is out of scope for this challenge. Response manipulation is fair game.
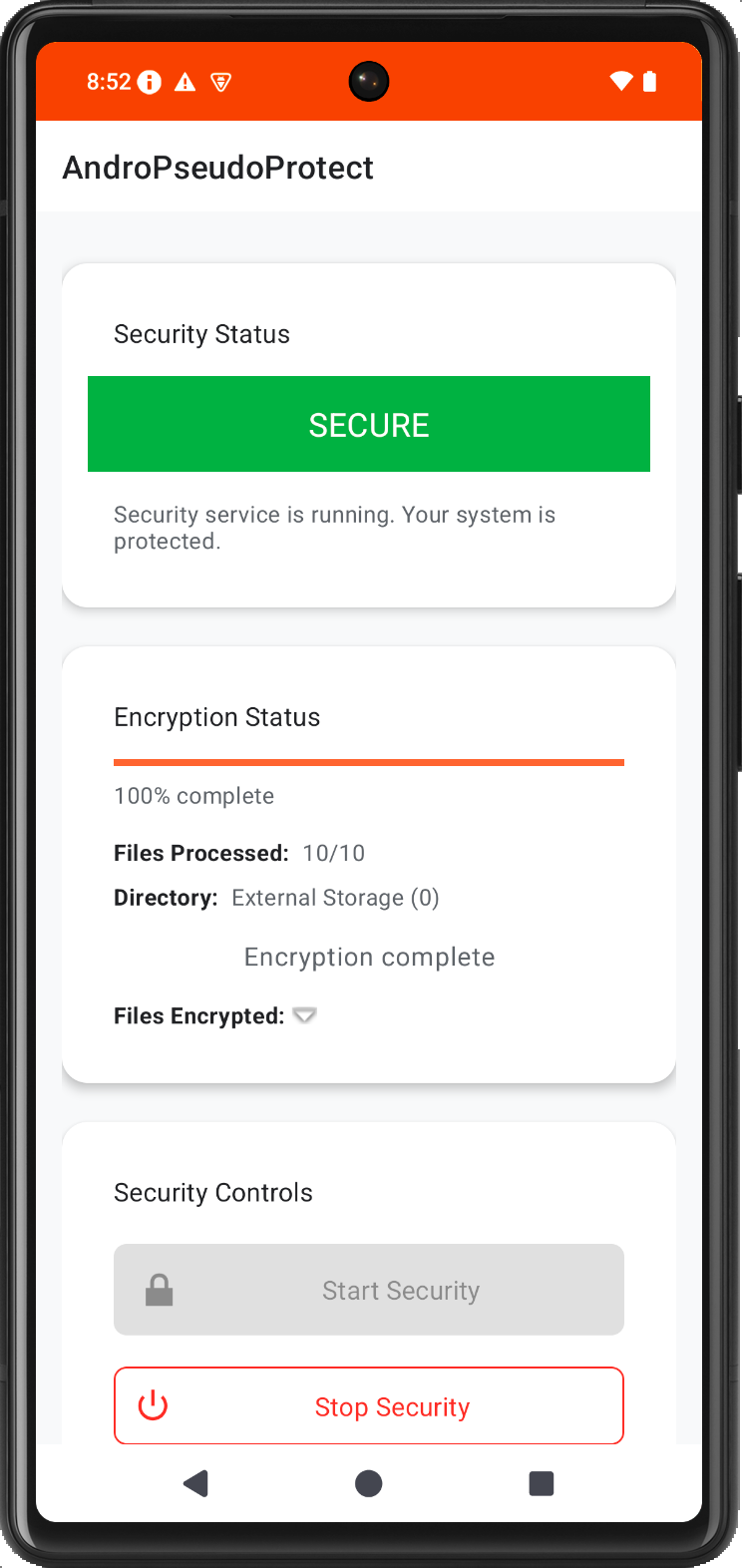
AndroPseudoProtect: Ultimate Device Security
Tired of worrying about your device security? AndroPseudoProtect offers comprehensive protection with just a tap! Our advanced security service monitors your device 24/7, providing real-time alerts through persistent notifications. With military-grade encryption and native code implementation for optimal performance, AndroPseudoProtect delivers peace of mind without draining your battery.
AndroPseudoProtect encrypts all files on your device's external storage to protect against unauthorized access. No more worrying about sensitive files you store on external storage. The intuitive interface lets you activate protection with one tap and includes secure authentication when disabling — ensuring only you control your device's security status.
Objective
Create a malicious application that exploits the AndroPseudoProtect application by targeting vulnerabilities in its IPC mechanisms. Your goal is to develop an Android application that can silently disable the encryption protection without the user's knowledge or consent. The attacker should also be able to steal unencrypted files otherwise considered encrypted on the external filesystem. The exploit should ensure that even when users believe they've activated the advanced protection, it remains ineffective because the victim application turns it off in the background, undermining the app's publicized security claims — all without notifying the victim.
Successfully completing this challenge demonstrates a critical vulnerability in service authentication that could allow attackers to silently disable security protections, putting sensitive user data at risk and potentially enabling further device compromise.
Restrictions: Your exploit must work on Android versions up to Android 15 and must not require any runtime permissions to be granted by the victim except the standard external storage access permissions and notification permissions on the device. Your attacker PoC should demonstrate the ability to extract and reuse any application-generated or hardcoded tokens from the victim application through normal user interaction, rather than hardcoding those tokens directly into the PoC.
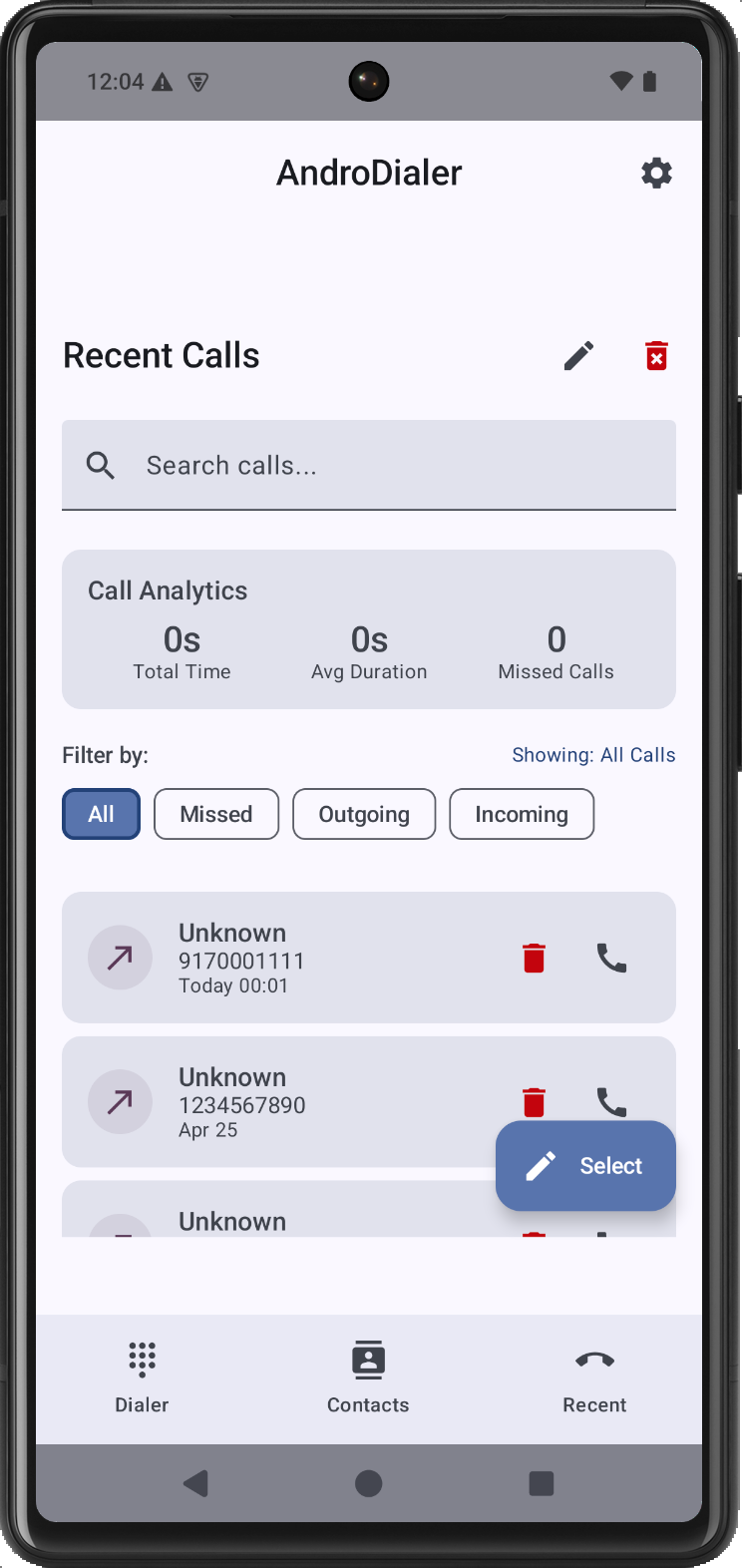
AndroDialer App: The Ultimate Phone Experience
Ever wanted to break free from the limitations of your regular Android dialer? Meet AndroDialer! A sleek, full‑featured dialer app that takes your calls to the next level.
It brings together smart contact organization, customizable quick‑dial widgets, and a “Business Focus” mode that filters interruptions so you stay in control of every conversation. Behind the scenes, AndroDialer delivers in‑depth call analytics to help you spot communication trends, plus enhanced security features. Its highly adaptable interface is complete with light and dark themes, call‑time limits, and fully personalized settings that strike the ideal balance of efficiency and elegance for both personal and professional calling.
Objective
Create a malicious application that exploits the AndroDialer application to initiate unauthorized phone calls to arbitrary numbers without the victim's knowledge or consent.
Successfully completing this challenge demonstrates a critical security vulnerability that could lead to financial fraud, privacy violations, and compromised communications security for AndroDialer users.
Restrictions: Your exploit must work on non-rooted Android devices running versions up to Android 15 and must not require any runtime permissions to be explicitly granted by the victim, making it appear harmless to users during installation.
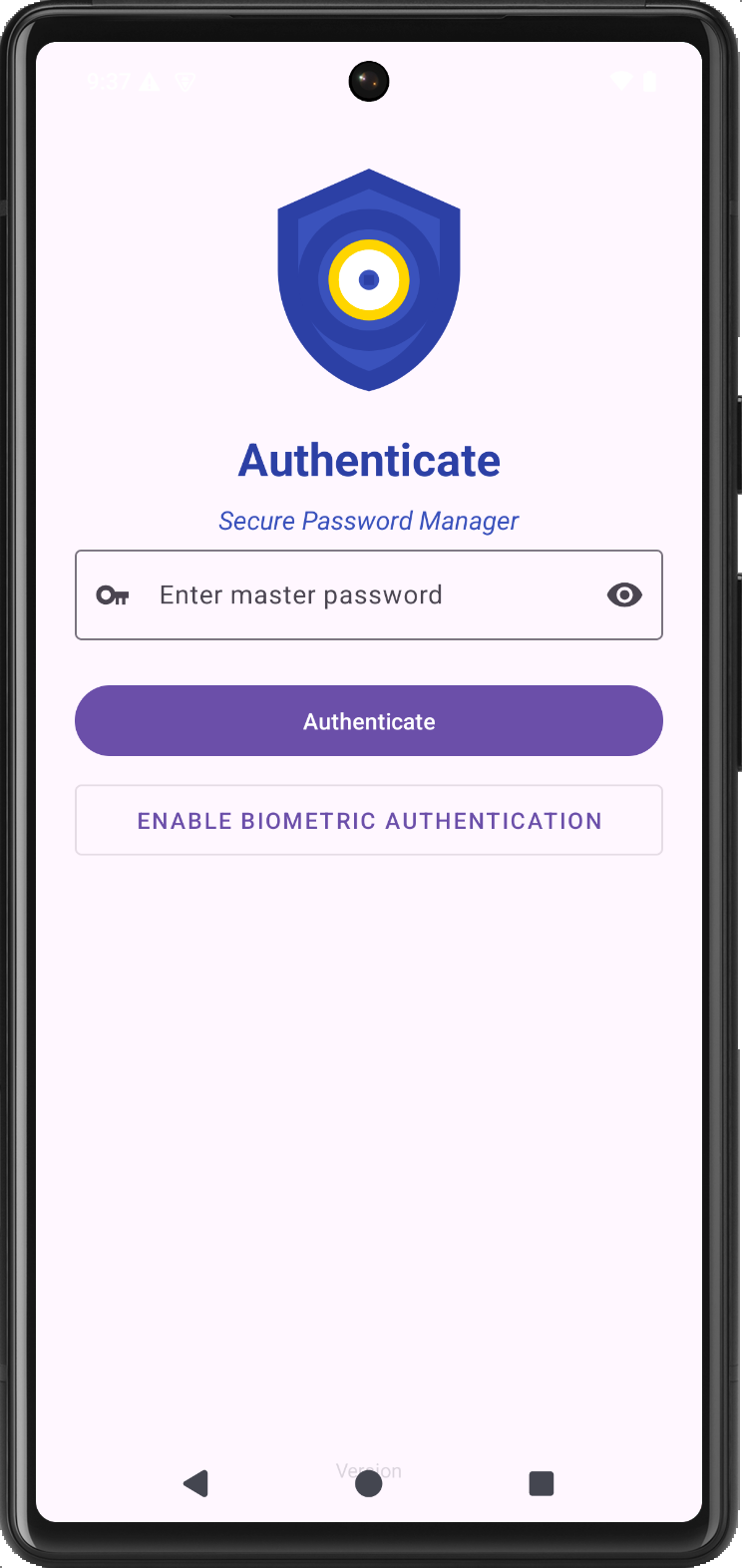
DroidCave: Secure Password Management
Tired of worrying about your password security? DroidCave offers a robust and intuitive password management solution for Android users. Store all your credentials in one secure location with military-grade encryption. Our clean, material design interface makes managing passwords effortless — create categories, generate strong passwords, and access your favorite sites with just one tap.
DroidCave encrypts all sensitive data using industry-standard methods, ensuring your passwords remain protected at all times. Never worry about remembering complex passwords again!
Objective
Create a malicious application that demonstrates your expertise in SQL injection and IPC mechanism exploitation to steal passwords stored in DroidCave, even when the user has enabled password encryption in the settings. Your goal is to develop an Android application with an innocent appearance that can, with just one click of a seemingly normal button, extract both plaintext passwords and the decrypted form of encrypted passwords from the DroidCave database.
Successfully completing this challenge demonstrates how seemingly secure password managers can be compromised through common vulnerabilities, potentially leading to widespread credential theft across multiple services.
Restrictions: Your POC Android exploit APK must work on Android versions up to Android 15 and should not require any additional permissions that the user must explicitly grant.
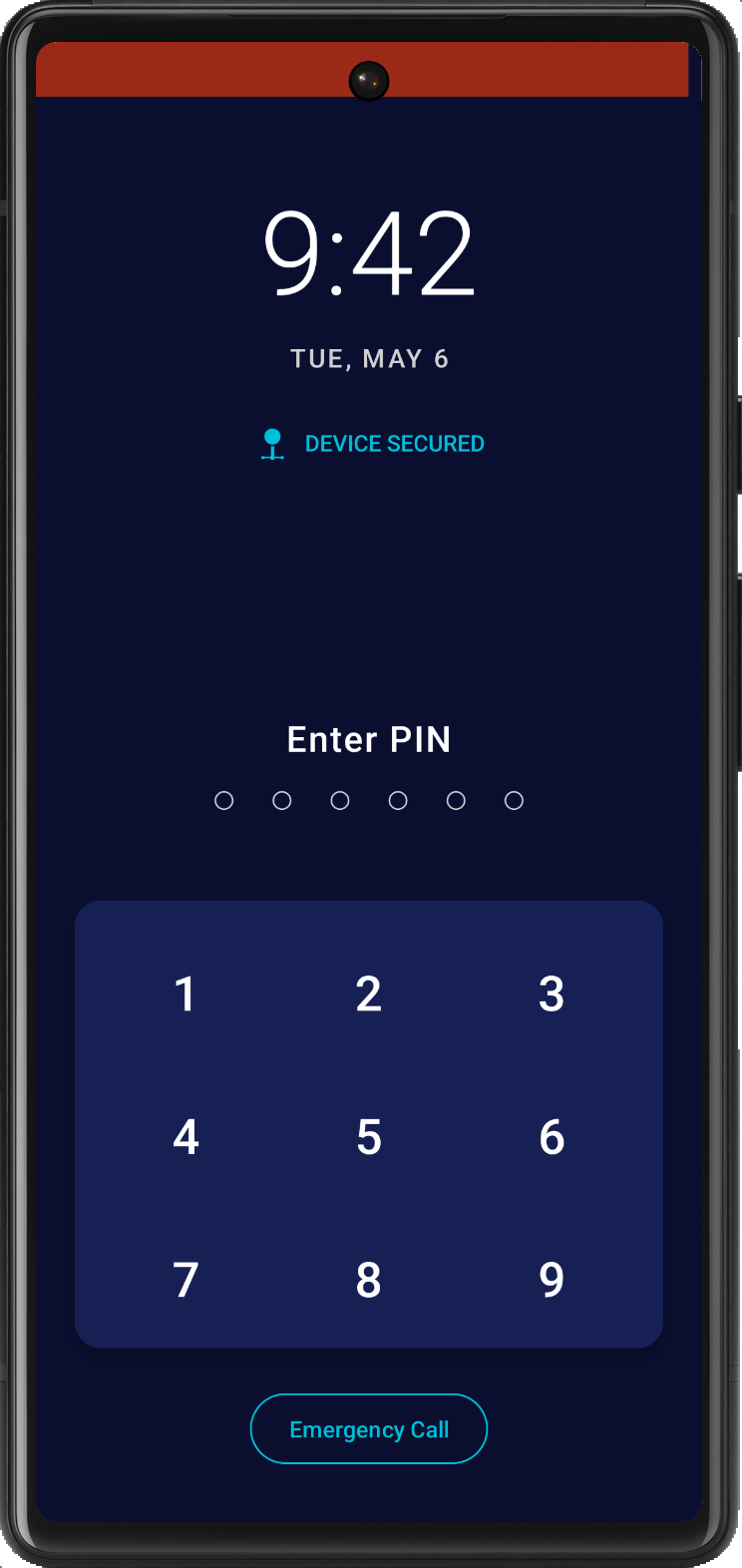
BorderDroid: International Border Protection
Crossing international borders as a highly targeted individual? BorderDroid provides the ultimate protection against unauthorized device seizures and searches. With our advanced security system, your sensitive data remains completely hidden from prying eyes. At the press of a button, BorderDroid activates a secure kiosk mode with a convincing but impossible-to-unlock interface that reveals nothing about your actual device contents.
BorderDroid's proprietary lockout system ensures that after multiple failed attempts, all sensitive traces of the product are automatically wiped, leaving no trace for unauthorized parties. You can also download our APK from our military-grade servers for installation on custom devices with minimal effort. The intuitive dashboard lets you control security features with ease, while our secret emergency exit protocol allows only you to regain access. With BorderDroid, maintain complete digital sovereignty even in high-pressure border crossing scenarios.
Objective
You are a Border Control agent who has intercepted a potential hacker based on their suspicious activity on the airport WiFi network. Your team has detained the suspect, but their device is locked using BorderDroid's advanced protection system. Intelligence suggests critical evidence is stored on this device. Your mission is to find a way to bypass BorderDroid's security mechanisms without triggering the data wipe countdown.
Successfully completing this challenge demonstrates a critical security flaw in BorderDroid that could be exploited by law enforcement to access protected devices during legitimate investigations, while also highlighting a vulnerability that malicious actors could potentially exploit.
Restrictions: The attack should not require root permissions on the device.
DroidPass: Ultimate Password Vault
Introducing DroidPass—the “secure” password manager that promises military-grade encryption for all your sensitive credentials! DroidPass uses advanced encryption techniques to store your passwords in a protected database, keeping them safe from prying eyes. Our intuitive interface lets you generate strong, unique passwords with just a tap, while our security module continuously monitors your device for threats.
DroidPass automatically detects if your device is running in a tampered environment and takes appropriate security measures to protect your data. With secure encryption keys and multiple layers of security, your passwords are protected by the most advanced security techniques available. The clean, modern interface makes managing your digital life effortless while keeping your sensitive information under lock and key.
Objective
Your goal is to statically reverse-engineer the DroidPass application to identify and extract the exact base encryption key used to secure the password database.
Successfully completing this challenge demonstrates the risks of relying on "security through obscurity" and highlights why proper key management is essential for secure applications. You’ll also learn techniques to manually parse an APK file rather than relying solely on dynamic analysis techniques.
Restrictions: What's the fun if you just dynamically print out the key by hooking the application? Real reverse engineers rely on their static analysis skills to understand code behavior without execution. You must solve this challenge using only static reverse engineering techniques.
No runtime instrumentation, hooking, or dynamic analysis is allowed. You are also disallowed from using automated tools that directly extract secrets.
DroidView: Ultimate Private Browsing Solution
Worried about your online privacy? DroidView provides unmatched protection for your browsing activities! Our advanced security solution routes all your traffic through the secure Tor network, ensuring complete anonymity. With military-grade encryption and a sleek, intuitive interface, DroidView delivers peace of mind without compromising performance.
DroidView automatically protects all your web browsing by routing traffic through Tor's secure network, making it impossible for advertisers, ISPs, or malicious actors to track your online activities. The user-friendly interface allows you to toggle protection with a single tap and includes secure token authentication when disabling, ensuring only you control your privacy settings.
Objective
Create a malicious application that exploits the DroidView application by targeting vulnerabilities in its Tor security service. Your goal is to develop an Android application that, when launched, silently disables the Tor protection without the user's knowledge and redirects them to an attacker-controlled website. The exploit should disable Tor routing and then exfiltrate sensitive information to a remote server with a maximum of one click. The information should include the victim's real IP address and device information. Why stop there? Try to get a complete list of applications installed on the device.
Successfully completing this challenge demonstrates a critical vulnerability in applications like these that promise security, but indirectly enables device identity unmasking while bypassing the privacy protections that users expect.
Restrictions: Your exploit must work on non-rooted Android devices running versions up to Android 15 and must not require any runtime permissions to be explicitly granted by the victim, making it appear harmless to users during installation. The informations mentioned in the objectives should be accomplished by exploiting "the WebView usage" in the DroidView application rather than directly through the malicious application. The information should be exfiltrated to a remote attacker controlled webserver.
DroidWars: The Plugins Race
Experience the thrill of battle in DroidWars, a customizable Android gaming platform where players can expand their gaming experience with powerful plugins! Download new characters, weapons, and abilities from our upcoming community marketplace to personalize your gameplay. Our innovative dynamic plugin system allows for seamless integration of new content without updating the main application.
Just use our new Refresh feature, and plugins are automatically loaded from the appropriate location, reducing the need for manual player interactions. DroidWars automatically discovers and loads them on startup. Join thousands of players in creating and sharing exciting new content for the ultimate gaming experience! Join us in this pre-release before we launch the full game!
Objective
Develop a malicious plugin that exploits DroidWars' vulnerable plugin loading mechanism. Your goal is to create a plugin that appears legitimate but contains hidden code that, when loaded in DroidWars, steals files stored on the SD card without requiring any additional permissions.
Successfully completing this challenge reveals a critical security vulnerability in dynamic code loading practices that could allow attackers to access sensitive user data, execute privileged operations, or even gain persistent access to the device through a seemingly innocent game plugin.
Restrictions: Your plugin must work on non-rooted Android devices running versions up to Android 15 and must not require any runtime permissions to be explicitly granted by the victim. The malicious plugin should appear as a legitimate game component, and must not break UI functionality while secretly stealing data from external storage in the background.
GeofenceGamble: The Ultimate Game of Speed
Embark on a thrilling adventure with GeofenceGamble! Explore your city to discover and collect virtual relics of varying rarities scattered across real-world locations. View collectibles on an interactive map, navigate to their locations, and press "Collect" when you're within range.
Compete with friends on the leaderboard as you hunt for the rarest relics. GeofenceGamble uses precise geolocation to ensure fair play and encourage outdoor exploration.
Objective
Bypass geofencing restrictions in location-based games like GeofenceGamble without requiring physical presence at target coordinates. Hackers are supposed to be lazy! Your goal is to identify and leverage weaknesses in the app's location verification system to collect virtual relics remotely.
These techniques should enable you to collect high-value relics from anywhere in the world, highlighting fundamental security issues in how mobile games implement location-based mechanics.
Successfully completing this challenge showcases vulnerabilities in GPS-dependent applications and emphasizes the need for implementing additional validation layers beyond simple coordinate checking.
Restrictions: Your solution must work on Android devices running versions up to Android 15. At no point should your solution require statically patching the application to bypass any protections. The exploit should be able to modify location data seamlessly without triggering the game's anti-cheat mechanisms or showing suspicious movement patterns that could flag an account for review.
ReconDroid: The Application Intelligence Provider
Ever wondered what secrets your Android device holds? Meet ReconDroid! A powerful application analysis tool that gives you unprecedented insight into your device's ecosystem. ReconDroid delivers comprehensive application reconnaissance with detailed technical analysis, storage insights, and component mapping.
It features smart filtering, real-time search, and professional-grade backup and export functionality for security researchers. Its streamlined interface helps you understand your device's attack surface while ensuring critical application intelligence is always accessible and shareable.
Objective
Create a malicious web page that exploits the ReconDroid application to exploit the Export functionality to extract sensitive application data and device information without the victim's knowledge or consent to an attacker controlled webserver.
Successfully completing this challenge demonstrates a critical security vulnerability that could lead to unauthorized data exfiltration, privacy violations, and exposure of sensitive application intelligence that could be used for targeted attacks against ReconDroid users.
Restrictions: Your solution must work on Android devices running versions up to Android 15. Your exploit must work through web browsers where all the victim needs to do is open a webpage on the Android devices browser and must not require any additional permissions beyond what ReconDroid already requests, making the attack vector appear as a legitimate web interaction to unsuspecting users.
After You Upload Your Solution:
Review
Certification
Recognition


Earn a Free Certification and Showcase Your Android Security Expertise
Outcomes & Takeaways
Practice reverse engineering, static and dynamic analysis, and bypassing security controls on real Android APKs.
Real-World Scenarios
Work with realistic apps ranging from password managers and dialers to privacy tools and geolocation-based games that mimic the complexity of production environments.
Tool Proficiency
Get comfortable using tools like Ghidra, Frida, Medusa, JADX, and more in a practical settings.
Security Mindset
Train yourself to think like an attacker: identify weaknesses, understand threat models, and build intuition around mobile app attack strategies and defense evasion.
Portfolio-Ready Experience
Build a strong foundation that you can showcase, whether you are applying for security roles or contributing to mobile app defense strategies.
Don’t Just Hack—Win!

FEATURED LINKS
POLICIES
CONNECT WITH US
-
Twitter
-
LinkedIn
We’ve updated the submission guidelines for our Free Challenges
Live Trainings list:
Lead Application Penetration Tester*
A Cybersecurity Testing & Consulting Firm
$150,000 - $180,000 a year
Required Qualifications & Skills
- Bachelor’s degree in Computer Science, Software Engineering, or related field, or equivalent job experience
- Thorough security testing of developer workflows and mobile applications (iPhone and Android), including identification of security issues and vulnerabilities
- Proficiency in multiple programming languages and understanding of secure coding practices
- In-depth source code reviews to identify security flaws or weaknesses that could be exploited in software applications
- Detailed assessments and compilation of findings into reports for further review and action
- Experience with tools like Burp Suite Pro, Checkmarx, Corellium, Synopsys, Acunetix, VeraCode, SAST & DAST Tools, Plextrac, Cloud security (AWS / Azure / Oracle), Postman, SmartBear ReadyAPI, SoapUI, and Hashicorp Vault
Key Responsibilities
- Team Leadership: Lead and mentor penetration testers, ensuring high-quality security assessments
- Mobile & DevOps Security: Conduct security testing of mobile apps (iOS/Android) and integrate security into DevOps pipelines
- Code & Penetration Testing: Perform source code reviews and comprehensive web/mobile penetration testing
- Reporting & Collaboration: Document findings in detailed reports and collaborate with development teams for remediation
- Offensive Security: Execute red team exercises and offensive security operations
- Security Strategy: Develop and implement security testing strategies and best practices
- Global Collaboration: Work with global teams to secure applications
- Automation: Automate security testing within CI/CD pipelines
iOS Application Security Engineer*
A Cyber-Risk Consulting Firm
$150,000 - $200,000 a year
Required Qualifications & Skills
- Proficiency in iOS frameworks (UIKit, Core Data) and Android frameworks
- In-depth knowledge of mobile security vulnerabilities (OWASP Mobile Top 10) and remediation techniques
- Familiarity with mobile security testing tools (e.g., MobSF, Drozer, Burp Suite, OWASP ZAP)
- Extensive experience in iOS application development using Swift/Objective-C, ideally also knowledge of Android (Java/Kotlin) security
- Strong understanding of cryptography principles, secure data storage, and key management
- Experience with mobile reverse engineering tools such as Frida
- Knowledge of App Store and Google Play Store compliance requirements
- Familiarity with advanced encryption techniques and secure app distribution
Key Responsibilities
- Security Architecture & Threat Modeling: Design secure architectures, perform threat modeling, and ensure compliance (OWASP, PCI DSS, NIST)
- Code Reviews & Auditing: Conduct code reviews, participate in security audits, and perform SAST/DAST
- Vulnerability Management & Penetration Testing: Manage vulnerabilities, conduct penetration tests, and analyze threats
Specialist, Offensive Android Security*
A Tech Giant Company
$151,200 - $207,500 a year
Required Qualifications & Skills
- Proficiency in tools for kernel debugging, fuzzing, and penetration testing
- Experience with reverse engineering tools (e.g., IDA Pro & Ghidra), debugging tools (e.g., JTAG/SWD)
- 5+ years of experience in system-level penetration testing and vulnerability research
- Strong knowledge of low-level programming languages such as C and Assembly
Key Responsibilities
Kernel Security Researcher*
$143,100 - $264,200 a year
Required Qualifications & Skills
- Background in secure coding and code auditing
- Knowledge of modern anti-exploitation mitigations and their effectiveness
- Programming background in C, C++, and Python
Preferred Qualifications:
- Knowledge of macOS and iOS security architectures
Key Responsibilities
Mobile Reverse Engineer*
$88,200 - $195,200 a year
Required Qualifications & Skills
- 5+ yrs experience in mobile software reverse engineering
- Experience with Windows, Linux, Android, OS X, and iOS operating system & architecture
- Experience in computer or cell phone architecture, system internals, operating systems, and/or boot process software engineering
Experience with static analysis tools such as IDA Pro, Ghidra and Binary Ninja
- Experience with debugging tools such as WinDbg
- Experience with virtualization, sandboxing, and emulation tools like VMware, KVM, QEMU and others
- Working knowledge of programming languages such as C, C++, .NET, Python, Java, etc.
- Experience debugging mobile application memory and performance issues
Preferred:
- Experience requiring a deep knowledge of Android and a strong passion in mobile industry and mobile development
- Experience developing/designing mobile phone platforms highly desired
- Experience in wireless API's (Wi-Fi, Bluetooth) preferred
- Engineer software scripts in C, C++, and Java with emphasis on prototyping and API extraction
Key Responsibilities
- Research new trends, techniques, and packaging of malicious software to stay current and ready to identify and handle zero-day exploits
- Research behavior of binaries and share detailed understanding of how apps behave at memory/register level in support of technical exploitation operations
- Support efforts to design, prototype, document, test, conduct exploitation automation and transition code analysis methods and tools specific to technical exploitation operations
Senior Lead Security Engineer - Mobile*
$147,700 - $190,000 a year
Required Qualifications & Skills
- Strong understanding of mobile application security risks and mitigation strategies for both Android and iOS platforms
- Experience in implementing or managing mobile security operations
- Familiarity with CI/CD pipelines, DevSecOps methodologies, and secure software development practices
- Ability to collaborate with development teams on security functions & resolutions
- Hands-on practical experience delivering enterprise level cybersecurity solutions and controls
- Strong collaboration and communication skills are essential for working effectively with teams on security implementations
- Ability to evaluate current and emerging technologies to select or recommend the best solutions for future state architecture & enterprise integrations
- Proven experience leading projects from scoping to delivery
Key Responsibilities
- Utilize our mobile security vendors and tools to drive proactive security measures, ensuring optimal configuration, monitoring, and maintenance to safeguard our mobile applications.
- Oversee the deployment, integration, and ongoing support of mobile security tools, ensuring they are effectively utilized and updated.
- Provide technical leadership in securing mobile applications and infrastructure, ensuring compliance with industry standards and best practices.
- Manage the lifecycle of mobile security tools, including planning and executing upgrades to maintain optimal performance and security.
- Work closely with cross-functional teams to enhance security awareness, provide training, and ensure adherence to security protocols. Additionally, serve as a key feedback conduit to the mobile binary scanning team, risk management, and source scanning teams, ensuring continuous improvements in security posture and alignment with organizational security strategies.
Reverse Engineer - Android*
$90,000 - $120,000 a year
Required Qualifications & Skills
- 3-5 years of hands-on experience with Android and reverse engineering
- In-depth understanding of Android internals and the ability to read, comprehend, and analyze source code software
- Familiarity with reverse engineering tools such as Jadx, Ghidra, Frida, IDA Pro, and Burp to perform binary and APK analysis
Key Responsibilities
To give you an idea of how this Reverse Engineer Malware Analysis - Android role would look and feel, here are some things you could expect to do:
- Review malicious applications and SDKs by analyzing, unpacking, and reverse engineering software that compromises Android devices
- Review security policy violations, vulnerabilities, or improper coding practices
- Research threats like APT using Open-Source Intelligence (Virus Total, Web, ExploitDB, MITRE, etc.)
Android Mobile Reverse Engineer*
$100,000 - $150,000 a year
Required Qualifications & Skills
- Expertise in reverse engineering tools
- Knowledge of Android internals
- Strong debugging and analysis skills
- Familiarity with encryption and obfuscation techniques
- Ability to work with disassemblers and debuggers
Desired Qualifications:
- Experience with Android emulator tools
- Familiarity with mobile penetration testing
- Experience with static and dynamic analysis tools
- Knowledge of security exploits in mobile apps
- Ability to develop custom reverse engineering scripts
- Strong communication and reporting abilities
Key Responsibilities
- Deconstruct mobile application code
- Identify and mitigate security risks
- Reverse engineer mobile app binaries
- Conduct security audits on Android systems
- Document findings and create reports
Mobile Implant Software Engineer*
$114,000 - $180,000 a year
Required Qualifications & Skills
- Demonstrated ability to perform advanced research and development on embedded systems, Linux, and iOS platforms
- Strong understanding of network protocols and experience in implementing support for TCP, UDP, and TLS
- Experience in designing, developing, and integrating modular cyber capabilities
- Proficiency in using and integrating CI/CD tools and practices
- Excellent problem-solving skills and the ability to design novel solutions to complex security challenges
- Strong leadership skills with the ability to guide and mentor development teams
- Programming Languages: C, C++, Python, Java, x86 Assembly, MIPS Assembly, Microblaze Assembly, ARM Assembly, ARM64 Assembly, VHDL, Verilog, XML, JSON, HTML
- Tools and Technologies: LLDB/LLVM, IDA Pro, Immunity Debugger, Immunity Canvas, Eclipse, Git, Subversion, Embedded Systems, FPGAs, Docker, Intel Performance Primitives (IPP), High Performance Computing (HPC), REDHAWK, OmniORB CORBA, Software Defined Radios (SDR), Signal Processing, MySQL, PostgreSQL, JDBC, Django, ActiveMQ, Jpype, Pyxb, STOMP
Key Responsibilities
- Design and implement innovative solutions to address operational security challenges
- Architect and develop flexible, modular cyber capabilities in C, C++, and Python
- Triage and analyze public software vulnerabilities (CVEs) for security concerns
- Provide technical support and custom solutions to high-priority customer needs
- Design and develop new client/server data distribution tools
- Implement support for multiple network protocols, including TCP, UDP, and TLS
- Create custom build systems and ensure portability using Docker
- Integrate new projects with CI/CD services to streamline development processes
- Generate and maintain unit tests to enhance the reliability of client/server applications
- Guide the development team in adhering to industry software engineering standards and best practices
iOS Vulnerability Engineer (Software)*
$120,000 - $170,000 a year
Required Qualifications & Skills
- Proficiency in reverse engineering tools
- Expertise in static and dynamic code analysis
- Familiarity with secure coding practices
- Proficiency in iOS development tools (e.g., Xcode)
- Ability to exploit and remediate vulnerabilities
Desired skills:
- Knowledge of ARM assembly
- Experience with fuzz testing methodologies
- Familiarity with jailbreak development
- Understanding of malware analysis techniques
- Expertise in cryptographic protocols
- Proficiency in scripting for automation (e.g., Python)
Key Responsibilities
- Develop mitigation strategies for discovered issues
- Conduct security assessments of iOS applications
- Perform reverse engineering of iOS binaries
- Collaborate with development teams to improve software security
- Document findings and recommend improvements
Android Security Engineer*
An IT Consulting and Services Firm
$115,000 - $165,000 a year
Required Qualifications & Skills
- Static Analysis - decompilation, dissasembly, code auditing
- Dynamic Analysis - debugging monitoring, fuzzing
- Sample Tools - IDA Pro, Ghidra, Radare2, Jadx, Fernflower, Smali, Baksmalu, ADB, JDWP, Android studio, bluestack, Frida, Wireshark, Cyberchef. HTTP interception, Yara, Snort
- Programming (Java/Kotlin, Scripting, Javascript, Encode/Decode, encryption and decryption)
- Android fundamentals (permissions, Manifest, Entry points, Broadcast receivers, exported activities, services, subclasses, Dalvik/ART Virtual machine)
Key Responsibilities
- Conducting static and dynamic analysis
- Providing assessment and evidence to support findings
- Assessing detection and analysis gaps as well as scalable enforcement through detection rules
Information Security Engineer (Android)*
A Large Online Media Provider
$197,000 - $291,000 a year
Required Qualifications & Skills
- 8 years of experience with security assessments or security design reviews or threat modeling
- 8 years of coding experience in one or more general purpose languages
Preferred qualifications:
- Knowledge in programming languages, compilers, static and dynamic analysis techniques
- Experience in Mobile App Development and Android Apps
- Experience implementing sand-boxing infrastructure or low-level systems features and building static analysis tools, linters or compilers
- Experience with open source
Key Responsibilities
- Review and develop secure operational practices, and provide security guidance for engineers and support staff
- Review designs and look for vulnerabilities, both with one-time reviews and longer term engagements
- Look for vulnerabilities with techniques including reverse engineering, fuzzing, and static analysis
- Respond to vulnerabilities with repos, mitigations, and hardening. Surface vulnerability patterns and design them out.
Sr. Android Penetration Tester*
Required Qualifications & Skills
- Strong understanding of malware, phishing attacks, attack vectors, and security best practices
- Knowledge of penetration testing tools, threat modeling, and security frameworks
- Ability to conduct security research, CVE analysis, and adversary simulation
- Strong communication skills to work cross-functionally with engineering and security teams
- Experience working in corporate environments with internal penetration testing teams (preferred over agency-based consulting experience)
- Bachelor’s degree in either Cybersecurity, Computer Science, Information Security, or related field
Preferred Qualifications:
- Certifications in offensive security
- Published CVEs, blog posts, or walkthroughs on security research
- Malware development and reverse engineering experience
- Experience working in top security consulting firms or in-house red teams at major tech companies
- Hands-on experience with firmware penetration testing and IoT security.
Key Responsibilities
- Plan, scope and conduct vulnerability assessment/ Penetration test on internal / external facing public assets such as Web application, Android platform, Android Apps, Backend APIs, and Cloud services
- Research & and conduct adversary simulation for known security threats and identify novel attack vectors to test a system’s relative security readiness
- Conduct Threat modelling, Threat Intelligence and scoping with stakeholders
- Assist in creating and maintaining internal penetration testing and practice within QA team, managing vulnerabilities and tracking until closure
- Build Test harness & required Automation suites and validate attack vectors in Threat Lab
- Co-ordinate with program management, security architects at Internal & offshore sites
- Stays up to date on current tools, technologies, and vulnerabilities to incorporate into testing practices
- Research and developing exploits for zero-day vulnerabilities
- Conduct penetration test on IOT and Firmware Devices
iOS Application Security Engineer*
$125,000 - $175,000 a year
Required Qualifications & Skills
- Bachelor’s degree in Computer Science, Information Security, or a related field, or 5+ years in mobile application development
- Extensive experience in iOS application development using Swift/Objective-C
- In-depth knowledge of mobile security vulnerabilities (OWASP Mobile Top 10) and remediation techniques
- Proficiency in iOS frameworks (UIKit, Core Data) and Android frameworks
- Familiarity with mobile security testing tools (e.g., MobSF, Drozer, Burp Suite, OWASP ZAP)
- Strong understanding of cryptography principles, secure data storage, and key management
Preferred Qualifications:
- Relevant security certifications
- Experience with mobile reverse engineering tools such as Frida
- Knowledge of App Store and Google Play Store compliance requirements
- Familiarity with advanced encryption techniques and secure app distribution
Key Responsibilities
iOS Engineer - Product Security*
$143,100 - $264,200 a year
Required Qualifications & Skills
- 2+ years of iOS app development experience in Swift and/or Objective-C
- Experience and/or strong interest in security/secure programming, digital signatures and PKI
- User interface programming experience with SwiftUI and/or UIKit
- Understanding of computer science fundamentals
- Able to thrive in a reciprocal environment and clearly communicate across teams
Preferred Qualifications:
- Self-motivated, critical, and detail oriented
- Strong debugging and analytical skills
- Familiar with the ISO 18013-5 standard is a plus
- Experience developing software with any of the following frameworks is a plus: ID Verifier API , Verify with Wallet API
- BS or MS in Computer Science, related technical field or equivalent experience
AI Security Engineer*
Required Qualifications
- 2+ years of programming experience in languages like Python, Ruby, Go, Swift, Java, .NET, C++, or another object-oriented language
Key Responsibilities
- Deliver AI security training sessions and provide guidance to internal development teams
- Offer architectural and design recommendations with an AI security focus
- Shape processes, priorities, and decision-making within your team and with partners to drive stronger security outcomes
Offensive AI Security Tester*
Required Qualifications
- Solid understanding of ML/GenAI concepts (LLMs, embeddings, diffusion models) and adversarial ML techniques (such as model extraction, data poisoning, and prompt manipulation)
- Background in cybersecurity red teaming or penetration testing, with strong skills in Python and scripting for automation and test framework development
- Knowledge of AI security standards and frameworks, including NIST AI RMF, MITRE ATLAS, or OWASP LLM Top 10
- Experience with AI/MLOps tools and enterprise integrations (Azure AI, AWS SageMaker, OpenAI API, Hugging Face, LangChain, or similar platforms)
Nice-to-Haves:
- Experience integrating AI with SIEM/SOAR platforms and threat intelligence monitoring
- Background in creating reusable adversarial testing assets, scripts, and automated workflows
Adversarial Prompt Expert*
Required Qualifications & Skills
- Creativity and persistence, with the ability to explore edge cases and iterate through multiple variations
- Strong documentation skills to record tests, track outcomes, and communicate findings clearly
- Solid ethical judgment, with an understanding of boundaries and responsible handling of sensitive material